Cybersafety – a key element in digital media literacy skills
National CyberDay 2023
October 2 marks ICTC’s National CyberDay 2023! Designed for maximum flexibility in timing and delivery with teachers and parents in mind, the online event features:
- The 10 Immutable Laws of Cybersafety
- How to Be #UnHackable tip sheets for grade K-3, grade 4-8 and grade 9-12 for in-class and at-home
- Lesson Plans for the month with digital media literacy lesson plans and activities for your classroom including topics like online privacy, cybersafety and device/account security, recognizing disinformation, digital citizenship, and many more
- Online resources including curriculum, videos, online games, and lesson plans from trusted and vetted sources
- All materials and resources will be available from October 2 for the entirety of the school year so that teachers and parents can integrate them at their convenience
Register your class or family to receive the materials in your inbox.

If you experience any difficulties with the registration process please email contact@KnowledgeFlow.org
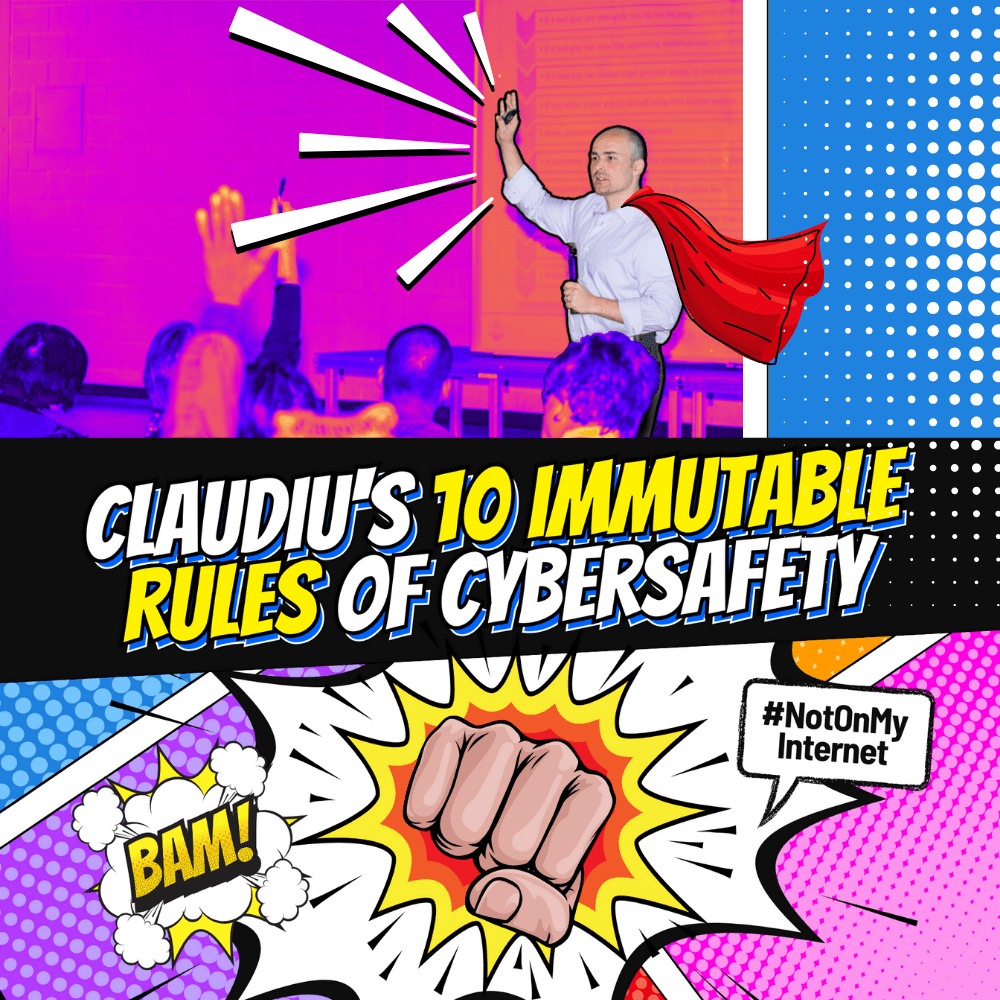
10 Immutable Rules
How to be UnHackable: Claudiu Popa’s 10 Immutable Rules for Cybersafety
- This webinar hosted by cybersecurity expert and KnowledgeFlow founder and CEO, Claudiu Popa is a can’t-miss for both teachers and students!
- Learn how to be #UnHackable online in 10 easy-to-follow steps.
Also included is a printable poster that serves as a reminder to students and teachers alike to apply these Immutable Rules in the classroom and at home.
Get your badge of allegiance to show your commitment to upholding these rules.
How to Be #UnHackable tip sheets
Designed with teachers and parents in mind, our cybersafety tip sheets are available to fit your schedule!
- Our How to Be #UnHackable cybersafety tipsheets have been customized for different age groups including: grades K-3, grades 4-8, grades 9-12, and for parents and guardians
- Topics include: First Principles of Cybersafety, internet safety basics, online gaming, social media management, online privacy, cybersafety and device/account security, recognizing disinformation, digital citizenship, online crimes, and so much more!
- Feel confident sharing these resources both at home and in the classroom, knowing they have been meticulously curated by cybersafety experts
- Incorporate them on your schedule. All tip sheets will be made available on October 2 and remain available for the entire academic year


Ready-To-Use lesson plans
A comprehensive collection of digital media literacy lesson plans created for K-12 educators, featuring a full month’s supply of ready-to-use materials for effortless incorporation into your classroom schedule and curriculum.
- Lesson plans cater to elementary (K-3), middle (4-8), and high school (9-12) grade levels
- Carefully curated by cybersafety experts from trusted and validated sources
- Topics include: Balancing time spent online, internet safety basics, online gaming, online privacy, cybersafety and device/account security, staying positive online, recognizing disinformation, digital citizenship, online crimes, and many more!
- These captivating, engaging, and comprehensive lessons were designed to be completed within 45-minutes or less, ensuring seamless integration into your current classroom schedule.
- Customized to suit your timetable! All lesson plans will be accessible beginning October 2nd and will remain available for the entirety of the academic year.

Partner Content
Our amazing cybersafety super hero partners have created games, videos and special offers just for National CyberDay Participants.
- CyberStart Canada
- CyberTitan
- EECD of New Brunswick
- Cyber Legends
- Logics Academy
- KnowledgeFlow

Resource Package
Registered participants will receive a complete resource package in their inbox, including:
- 10 Immutable Rules of Cybersafety Poster
- How to Be #UnHackable cybersafety tipsheets customized for grades K-3, 4-8, and 9-12
- Lesson Plans
- Credential Recognition Badge for participating teachers
- Certificate of Participation to distribute to students
- Incorporate them on your schedule. All tip sheets will be made available on October 2 and remain available for the entire academic year
Gain access for both your home and classroom, register today!
If you experience any difficulties with the registration process or do not receive the resource package in your email, please email contact@KnowledgeFlow.org
